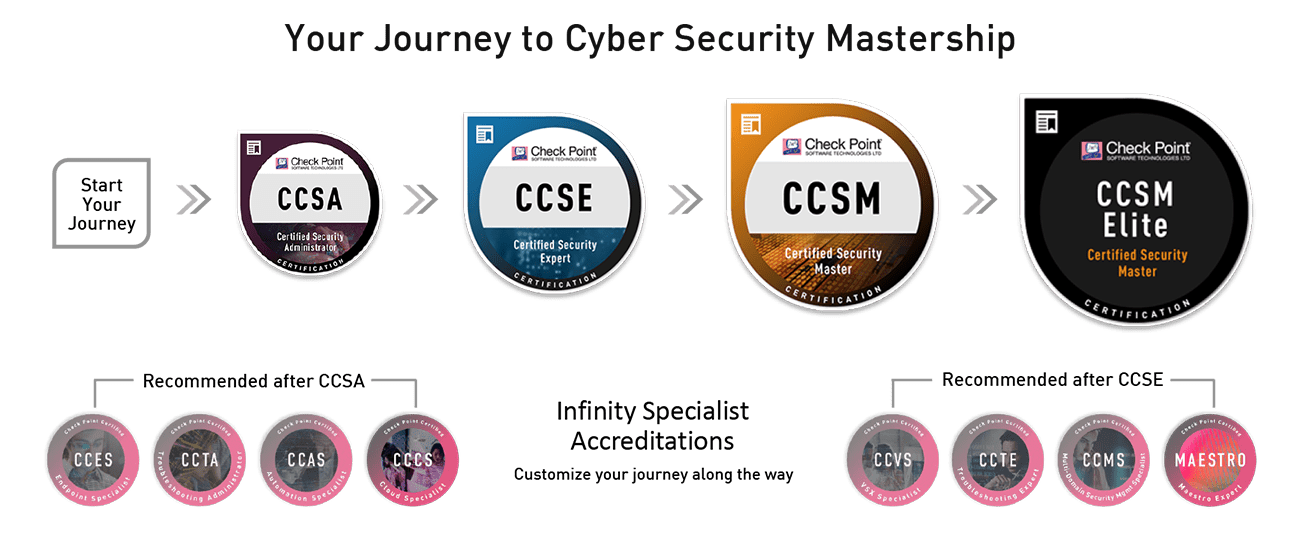
CheckPoint CCSA CCSE Bootcamp (CCSA-CCSE-Bootcamp) R81.10 – Fast Track Training for 5 days
About this Course
-
- Save 20% on your CCSA + CCSE Certification with this Fast Track Bundled Offer.
- Five-day course covers everything you need to start-up, configure and manage daily operations of Check Point Security Gateway and Management Software Blades systems on the GAiA operating system.
- Advanced course teaches how to build, modify, deploy and troubleshoot Check Point Security Systems on the GAiA operating system. Hands-on lab exercises teach h ow to debug firewall processes, optimize VPN performance and upgrade Management Servers. Validate and enhance your skills and optimally manage Check Point advanced security management systems.
Course Goals/Skills
- Know how to perform periodic administrator tasks
• Describe the basic functions of the Gaia operating system
• Recognize SmartConsole features, functions, and tools .
• Describe the Check Point Firewall infrastructure
• Understand how SmartConsole is used by administrators to grant permissions and user access
• Learn how Check Point security solutions and products work and how they protect networks
• Understand licensing and contract requirements for Check Point security products
• Describe the essential elements of a Security Policy
• Understand the Check Point policy layer concept
• Understand how to enable the Application Control and URL Filtering software blades to block access to various applications
• Describe how to configure manual and automatic NAT
• Identify tools designed to monitor data, determine threats and recognize opportunities for performance improvements
• Identify SmartEvent components used to store network activity logs and identify events
• Know how Site-to-Site and Remote Access VPN deployments and communities work
• Explain the basic concepts of ClusterXL technology and its advantages - Articulate Gaia system management procedures.
• Explain how to perform database migration procedures.
• Articulate the purpose and function of Management High Availability.
• Describe how to use Check Point API tools to perform management functions.
• Articulate an understanding of Security Gateway cluster upgrade methods.
• Discuss the process of Stateful Traffic inspection.
• Articulate an understanding of the Check Point Firewall processes and debug procedures.
• Describe advanced ClusterXL functions and deployment options.
• Explain how the SecureXL acceleration technology enhances and optimizes Security Gateway performance.
• Describe how the CoreXL acceleration technology enhances and improves Security Gateway performance.
• Articulate how utilizing multiple traffic queues can make traffic handling more efficient.
• Describe different Check Point Threat Prevention solutions for network attacks.
• Explain how SandBlast, Threat Emulation, and Threat Extraction help to prevent security incidents.
• Recognize alternative Check Point Site-to-Site deployment options.
• Recognize Check Point Remote Access solutions and how they differ from each other.
• Describe Mobile Access deployment options.
Intended Audience
- Technical professionals who need to deploy and manage Endpoint Security within their security environment.
Course Format


Language: English or Bulgarian
Course Materials:Digital Format. Lifetime Access. Official Learning Material from Check Point.
Lab: Individual Environment for each Delegate.


Course Duration
- 5 working days (09:00 – 17:00 / 9:00 am – 5:00 pm) UTC +2 (contact us for another Time Zone)
or
- 40 learning hours after hours (2 weeks, classes are held 4 times a week in one of the following options):
- Sat. and Sun. 10:00 – 14:00 or 14:00 – 18:00 or 18:00 – 22:00
- Mon. and Wed. 19:00 – 23:00
- Tue. or Thu. 19:00 – 23:00
Payments
You can enroll with your Check Point Learning Credits.
If you are Check Point Partner you can also get free training via the Co-op Program. Check your eligibility and request funds here or For any further questions or additional assistance, please E-Mail: [email protected]
We provide Invoices for Company Sponsored Trainings.
Invoices can be requested up to 7 days after the payment.
Course Schedules
[tribe_events_list category=”ccsa-ccse-bootcamp”]
Other Check Point Classes
[tribe_events_list category=”check-point”]
[tribe_event_countdown slug=”ccsa” show_seconds=”yes”]
If you dont see a date, contact us.
All classes are confirmed individually after enrollment.
Course Prerequisites
-
-
- Basic knowledge of networking
- 6 months to 1 year of experience with Check Point products recommended
-
This Training will Prepare you to take the following Certification Exams (exam price included)
- Check Point Certified Security Admin (CCSA) R81.x
- Check Point Certified Security Expert (CCSE) R81.x
- You can Certify Online or at our Test Center.
Course Objectives:
• Identify key components and configurations
• Create and confirm administrator users for the domain
• Validate existing licenses for products installed on your network
• Create and modify Check Point Rule Base objects
• Demonstrate how to share a layer between Security Policies
• Analyze network traffic and use traffic visibility tools
• Monitor Management Server States using SmartConsole
• Demonstrate how to run specific SmartEvent reports
• Configure a SmartEvent server to monitor relevant patterns
• Configure and deploy a site-to-site VPN
• Configure and test ClusterXL with a High Availability configuration
• Understand how to use CPView to gather gateway information
• Perform periodic tasks as specified in administrator job descriptions
• Test VPN connection and analyze the tunnel traffic
• Demonstrate how to create custom reports
• Demonstrate how to configure event Alerts in SmartEvent
• Utilize various traffic visibility tools to maintain Check Point logs
Perform an upgrade of a Security Management server in a distributed environment.
Use the migrate_export command to prepare to migrate a Security Management Server.
Deploy a Secondary Management Server.
Demonstrate how to define new network and group objects using the Check Point API.
Perform an upgrade of Security Gateways in a clustered environment.
Use Kernel table commands to evaluate the condition of a Security Gateway.
Use common commands to evaluate the condition of a Security Gateway.
Configure Virtual MAC.
Demonstrate how SecureXL affects traffic flow.
Describe how the CoreXL acceleration technology enhances and improves Security Gateway performance.
Demonstrate how to monitor and adjust interface traffic queues.
Identify specific threat protections used by Check Point Threat Prevention.
Demonstrate how to enable Mobile Access for remote users.
Curriculum
- 25 Sections
- 148 Lessons
- 999 Weeks
- Chapter 1: Introduction to Check Point Technology3
- Chapter 2: Introduction to Check Point Deployment5
- Chapter 3: Check Point Security Management Operations6
- Chapter 4: Check Point Licensing4
- Chapter 5: Security Policy Management8
- Chapter 6: Policy Layers4
- Chapter 7: Application Control & URL Filtering6
- Chapter 8: User Access Management8
- Chapter 9: Network Address Translation3
- Chapter 10: Traffic Visibility3
- Chapter 11: Monitoring System States2
- Chapter 12: Threat Prevention7
- Chapter 13: Management Upgrade and Migration8
- 14.1Upgrading Security Management Servers
- 14.2Upgrade / Download Wizard
- 14.3Check Point Upgrade Service Engine (CPUSE)
- 14.4CPUSE Upgrade Method
- 14.5Advanced Upgrade with Database Migration
- 14.6Installing Hotfixes and Major Version Upgrades
- 14.7Lab 13.1: Preparing for a Security Management Server Upgrade
- 14.8Lab 13.2: Upgrading the Security Management Server
- Chapter 14: Management High Availability4
- Chapter 15: Security Gateway Upgrade5
- Chapter 16: Advanced Check Point Maintenance6
- Chapter 17: Security Gateway Operations7
- Chapter 18: Policy Installation3
- Chapter 19: Gaia and Management APIs4
- Chapter 20: Acceleration4
- Chapter 21: Site-to-Site VPN10
- 22.1Introduction to VPN
- 22.2Internet Key Exchange (IKE)
- 22.3Site-to-Site VPN
- 22.4VPN Communities
- 22.5Domain Based VPN
- 22.6Access Control for VPN Traffic
- 22.7Configuring Site-to-Site VPN
- 22.8Externally Managed Certificate Authentication
- 22.9Lab 21.1: Configuring a Locally Managed Site-to-Site
- 22.10Lab 21.2: Configuring a Site-to-Site VPN with an Interoperable Device
- Chapter 22: Remote Access VPN11
- 23.1Introduction to Remote Access VPN
- 23.2Authentication
- 23.3Remote Access Clients
- 23.4License Requirements
- 23.5Client to Gateway Communication Challenges
- 23.6Secure Configuration Verification
- 23.7Desktop Security
- 23.8Multiple Entry Point (MEP) for Remote Access
- 23.9SSL Network Extender
- 23.10Configuring Remote Access VPN
- 23.11Lab 22.1: Configuring Remote Access VPN
- Chapter 23: Mobile Access VPN6
- Chapter 24: Clustering13
- 25.1Introduction to Cluster and ClusterXL
- 25.2ClusterXL
- 25.3Virtual IP Addresses
- 25.4Virtual MAC Addresses (VMAC)
- 25.5Cluster Synchronization
- 25.6Cluster Failover and Status Commands
- 25.7Cluster Traffic Flows
- 25.8Cluster Control Protocol (CCP)
- 25.9Sticky Connections
- 25.10Configuring a Security Gateway Cluster
- 25.11NAT and Proxy ARP for Clusters
- 25.12Lab 24.1: Configuring a High Availability Cluster
- 25.13Lab 24.2: Working with ClusterXL
- Chapter 25: Advanced Logs and Monitoring8